REWARD FOR REPORTING
If you find a security issue with our cloud services; and depending on what you have found we will then check it and if valid reward you!
See the Reporting an Issue section at the bottom of this page for instructions on how to report.
Please read the sections below below reporting an issue.
Thanks,
ibCom Protection Team
Our approach to security
Standard techniques to protect against
Standard Reward Rates
Based on confidentiality, integrity & availability.
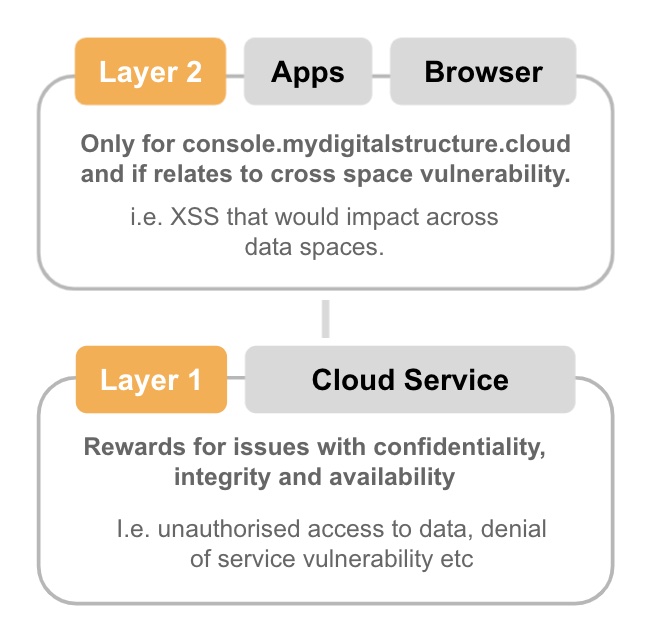
When reporting please reference which layer you are reporting on, see diagram below and also please check the updates page to ensure what you are reporting is not already covered in a future update.
Please also make sure you have completed the Quick Start Guide so you understand the platform & authentication design.
Attacks on self (i.e. vulnerabilities that only impact you in layer 2) are not rewardable. You need to show how they impact other users or the layer 1 cloud service.
| Level / Impact |
AUD |
| [RL1] Low Level report that could have a minor impact on availability of the ibCom cloud service but no impact on confidentiality & integrity for less than 5 minutes. |
$50 |
| [RL2] High Level report that has minor impact on availability of the ibCom cloud service but no impact on confidentiality & integrity for more than 5 minutes. |
$250 |
| [RL3] Low Level report that has impact confidentiality & integrity of the user. ie it could be used as part of an attack in the UI against the user ie phishing, click-jacking. But does not impact the ibCom cloud service. |
$50 |
| [RL4] High Level report that has impact confidentiality & integrity on the ibCom cloud service. |
$250+, but depends on the impact. Confirmed at time of report. |
| [RL0] Any report that has already been reported and in the process of being corrected. |
$0 |
By Design / Known
And thus not rewardable.
| Man in the middle attack; http v https |
We run marketing websites that still require http access, but all requests to our authentication endpoint logon (ie where u/p is sent) is via https only and uses perfect forward security - more ... |
| Large amounts of data |
Our firewall has blocking at the endpoint level for excessive data loads that may be an attempt to impact availability and thus in their own right do not have an impact. This is also combined with DDOS protection. We use AWS Web Application Firewall (WAF). Even if the User Interface is not checking the length. |
| IFRAME injection |
Protected by WAF. |
| /jscripts Directory Listing |
The /jscripts folder is a public JavaScripts files folder and has the listing enabled by design. |
| DMARC for Emails |
We understand the value of DMARC and are in the process of adding to the existing SPF DNS records - more ... |
| Cookies (httpOnly/secure) |
There are cookies with no secure & httpOnly flag which we ignore and are not used to within the security systems. We use the cookies marked as httpOnly and only accept requests over https. |
Layers
When reporting you need to include the layer for which you are reporting. Layer 2 apps built on top of the ibCom cloud services are not the responsibility of ibCom, except for our console app.
Payment
Payment is via PayPal or to an ADA wallet. We do not do direct bank account transfers.
|


