|
Cryptography is the practice and study of techniques for secure communication in the presence of third parties (called adversaries) - wikipedia
In relation to mydigitalstructure the focus is on at-rest protection that can be gained via the use of cryptography - given the in-transit protection is inherent in the use of https/SSL protocols.
mydigitalstructure is non-prescriptive in the cryptography scheme you choose to implement as the application owner - mydigitalstructure does provide some helper methods for storing keys and ciphertext (hashes, encypted data etc)
The mydigitalstructure SDK has utility functions that use the crypto-js library and the AES algorithm within its _util.protect namespace.
|
| AT-REST PROTECTION USE CASES |
| Ensure data has not been manipulated by any 3rd party (adversary).
Protect against manipulation at the lowest level.
|
ie.
Create a hash of the data record using the private key and store on the record.
On retrieval from the hosted model (mydigitalstructure) the View-Controller checks the hash before using the data.
|
Use
CORE_PROTECT_CIPHERTEXT
to store the hash (signature) in the context of the data.
|
| Encrypt sensitive data.
Protect against non-authorised disclosure at the lowest level.
|
ie.
Store public key in mydigitalstructure space.
Encrypt data using stored public key for at rest protection of sensitive data.
Decrypt data using Javascript & matching private key stored locally.
|
Store your generated public key within your space on mydigitalstructure using
CORE_PROTECT_KEY
|
|
|
CRYPTOGRAPHY MECHANISMS COMMONLY USED
IN ENTERPRISE APPLICATION SECURITY
|
|
EXAMPLE 1
SYMMETRIC (SINGLE KEY)
DATA MANIPULATION PROTECTION PATTERN
WITH MVC & MYDIGITALSTRUCTURE |
|
Add hashed signature to data record using symmetric cryptographic pattern (single private key):
- Generate a private key
- Store on the secure local device using Web Browser localStorage API.
- Retrieve the key and using select data record attributes (typically includes modifieddate etc) create SHA-512 hash (acting as digital signature)
- POST to mydigitalstructure using CORE_PROTECT_HASH_MANAGE
Check hashed signature
- Get the private key using the localStorage API
- Get the data record and hash using SHA-512
- Get the existing hash (signature) using CORE_PROTECT_CIPHERTEXT_SEARCH
- Check the just created hash and existing hash and if match data is valid (un-manipulated)
If you have multiple users within the space and they need to share the data, then you need to distribute the keys to each of them, unsually in a pem formated file.
Don't use mydigitalstructure to store the private key - as it reduces the value of the protection.
|
EXAMPLE 2
SYMMETRIC (SINGLE KEY)
DATA MANIPULATION PROTECTION PATTERN
WITH MYDIGITALSTRUCTURE & THE BLOCKCHAIN |
|
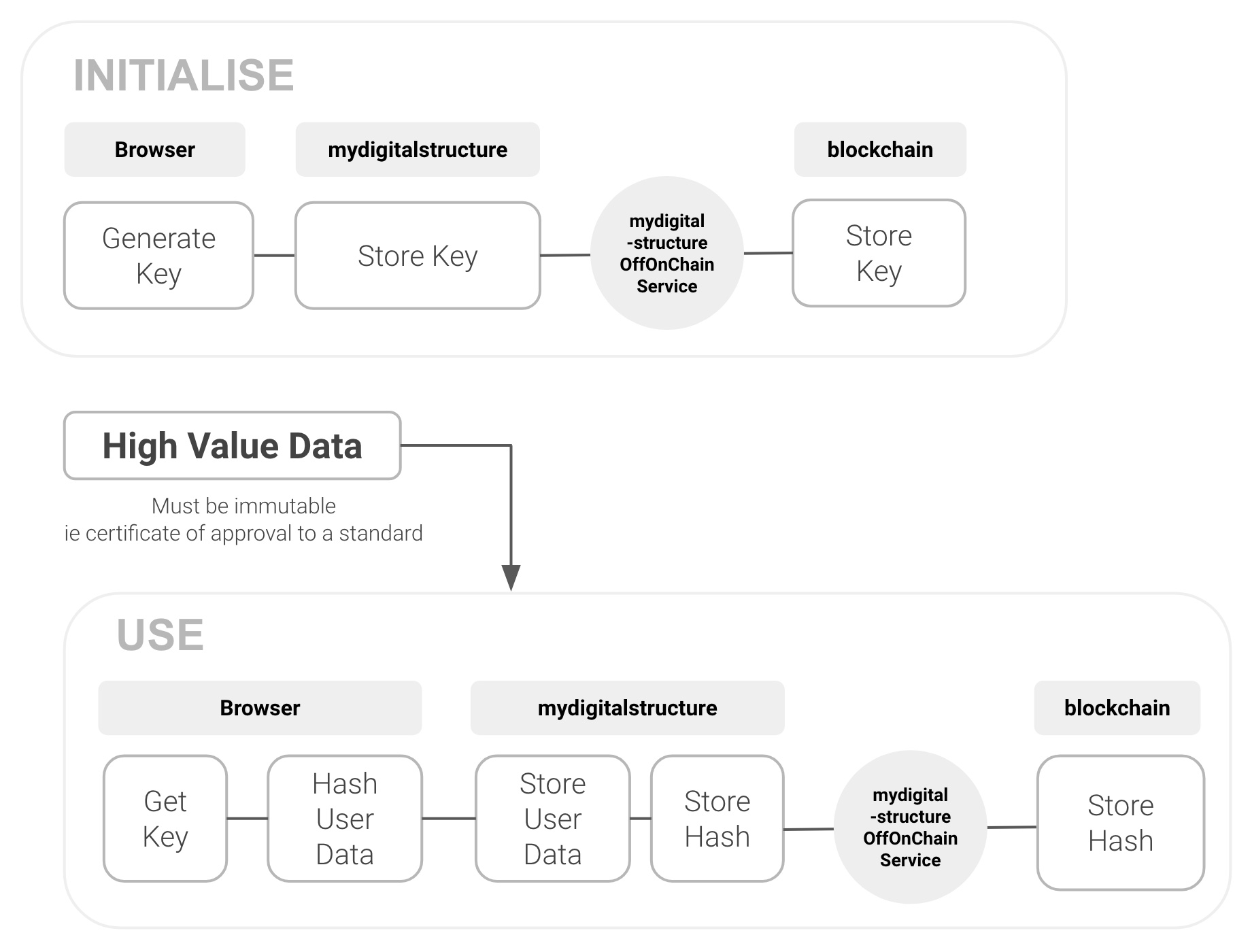
Store a hashed signature of the data using symmetric cryptographic pattern (single key) and the blockchain (for immatibility):
- Generate a key
- Store the key on the secure mydigitalstructure service using CORE_PROTECT_KEY_MANAGE api method.
- Store the key on the blockchain
- Retrieve the key using CORE_PROTECT_KEY_SEARCH and using select data object attributes (typically includes modifieddate etc) create SHA-512 hash (acting as digital signature)
- POST the actual data record to mydigitalstructure using object _MANAGE method (ie ACTION_MANAGE)
- POST the hash to mydigitalstructure using CORE_PROTECT_CIPHERTEXT_MANAGE
- POST the hash to the blockchain
Check hashed signature
- Get the key using CORE_PROTECT_KEY_SEARCH or from the blockchain (based on known public blockchain address)
- Get the data record and hash using SHA-512 and key
- Get the existing hash (signature) from the blockchain
- Check the just created hash and existing hash and if match data is valid (un-manipulated)
! Note: Instead of using the browser you could do the key generation and user data hashing using a node service (or a like).
|
|
|
EXAMPLE 3
ASYMMETRIC (KEY PAIR)
DATA MANIPULATION PROTECTION PATTERN
WITH MVC & MYDIGITALSTRUCTURE |
| Less strict than example 2, as some of the knowledge (public key) is stored on mydigitalstructure, as only concerned with in-transit manipulation and don't trust SSL or over non-encrypted connection.
You could use this with the MESSAGING_CONVERSATION endpoint where want message (posts & comments) integrity. ie when viewing the post/comment and with the correct private key, you can be ensured it has not been manipulated in-transit.
Add hashed signature to data record using asymmetric cryptographic pattern (public-private key):
- Generate a public / private key pair
- Store the private key on the secure local device using Web Browser localStorage API.
- Store the public key on the secure mydigitalstructure service using CORE_PROTECT_KEY_MANAGE api method.
- Retrieve the "public" key using CORE_PROTECT_KEY_SEARCH and using select data record attributes (typically includes modifieddate etc) create RSA/SHA-512 hash (acting as digital signature)
- POST the actual data record to mydigitalstructure using object _MANAGE method (ie INVOICE_MANAGE)
- POST the hash to mydigitalstructure using CORE_PROTECT_CIPHERTEXT_MANAGE
Check hashed signature
- Get the private key using the localStorage API
- Get the data record
- Get the existing hash (signature) using CORE_PROTECT_CIPHERTEXT_SEARCH
- Decrypt using the private key
- Check the decrypted select data attributes match select data attributes retrieved.
|
EXAMPLE 4
ASYMMETRIC (KEY PAIR)
DATA DISCLOSURE PROTECTION PATTERN
WITH MVC & MYDIGITALSTRUCTURE |
|
Using a public key stored on mydigitalstructure to protect data, beyond the existing authentication and authorisation mechanisms within mydigitalstructure.
ie if need to store sensitive data in regards to an individual or organisational IP etc - store it "off-object" and merge back in (object data is meta data).
Add hashed signature to data record using asymmetric cryptographic pattern (public-private key):
- Generate a public / private key pair
- Store the private key on the secure local device using Web Browser localStorage API.
- Store the public key on the secure mydigitalstructure service using CORE_PROTECT_KEY_MANAGE api method.
- Retrieve the "public" key using CORE_PROTECT_KEY_SEARCH and using select data record attributes (typically includes modifieddate etc) create RSA/SHA-512 encrypted data.
- POST the hash to mydigitalstructure using CORE_PROTECT_CIPHERTEXT_MANAGE. You could also create an text type structure element and store it there - it could then be retrieved as part of the generic advanced search (although not searchable) and decrypted by the client with the private key.
Do not save the data attributes that you are protecting to the data record - they are being saved in the ciphertext.
Check hashed signature
- Get the private key using the localStorage API
- Get the data record
- Get the data record hash using CORE_PROTECT_CIPHERTEXT_SEARCH
- Decrypt using the private key
- Add the data to object data record.
|


